Table of contents
- What is VPC?
- Use cases of VPC
- Subnets:
- Internet Gateway
- Network Address Translation (NAT)
- Route Table
- Classless Inter-Domain Routing (CIDR)
- NACL Network Access Control Lists
- Security Group:(Whom to allow/deny can be set through SG)
- VPC Dashboard:
- Private IP address Classes:
- DHCP(Dynamic Host Configuration Protocol)
- NTP:(Network Time Protocol)
- DNS(Domain Name Space)
- OSI Model in a Nutshell
- Egress-only Internet gateway.(IPV6)
- Stateless/Stateful Protocol:
- Ports:
- VPC Hands on:
- Here is your own Network!
- VPC Peering
What is VPC?
A Virtual private cloud (VPC) is a private cloud located inside a public cloud that enables you to experience the benefits of a virtualized network while using public cloud resources.
You have complete control over your virtual networking environment, including a selection of your IP address range, the creation of subnets, and configuration of route tables and network gateways.
Purpose of VPC is expose your server to the world.
Use cases of VPC
Using VPC, you can host a public-facing website, a single-tier basic web application, or just a plain old website.
VPC will manage Networking in AWS.
The connectivity between our web servers, application servers, and database can be limited by VPC with the help of VPC peering.
By managing the inbound and outbound connections, we can restrict the incoming and outcoming security of our application.
Subnets:
A subnet is a smaller portion of the network that typically includes all the machines in a certain area.
We can add as many as subnets we need in one availability zone. Each subnet must reside entirely within one availability zone.
The public subnets will be attached to Internet Gateway which enables Internet access.
The private subnets will not have internet access.
Each and every subnet which is presented in VPC must be associated with the routing table.
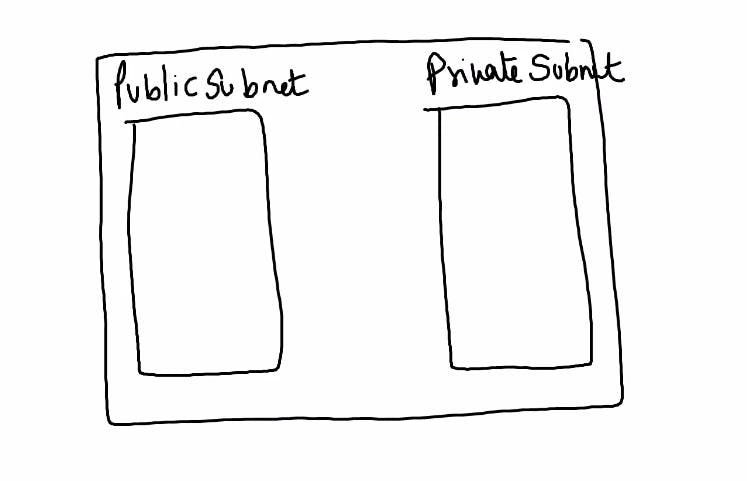
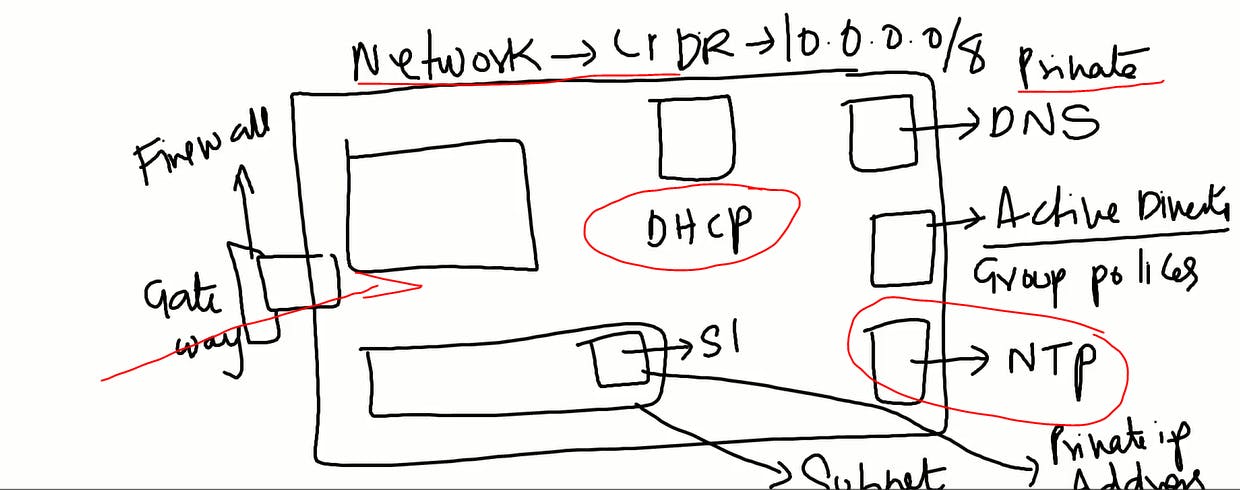
As shown in below diagram,VPC is divided into 2 subnets Public Subnet and Private Subnet.
1.Public Subnet:Your network exposed to the world and by default it gets internet.
2.Private Subnet:If you do not want to expose your server to the world that means no internet.
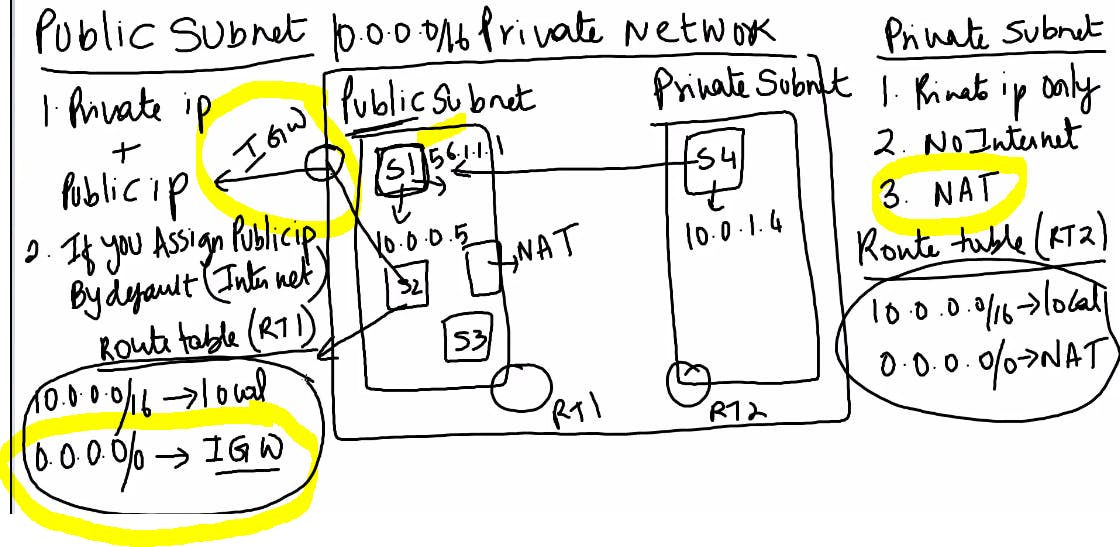
So,Lets deep dive more into VPC.
VPC has divided into two subnets as explained above.
Public IP is exposed to the world and internet available for this server no extra things to do.
Suppose if you hit google.com from it will directly gets connected through Internet Gateway(IGW) in Public IP.
For Private IP,It will be different case as your network is limited to you in this case if you need internet or expose to the world then NAT will comes in the picture.
NAT:For Private IP NAT will create public IP and act as mediator to expose your public IP to the world or to connect the internet.
That means as shown in below diagram,NAT has created one server over Public IP to connect with internet for Private IP this is how Private subnet gets connected to the Internet.
Internet Gateway
With the help of IGW (Internet Gateway), the resources present (e.g: EC2) in the VPC will enable to access the Internet.
One VPC can’t have more than one IGW
If resources are running in a certain VPC then IGW can not be detached from that particular VPC.
Network Address Translation (NAT)
An internal host can communicate with an internet server with help of NAT.
The internet and a private network are separated by a NAT device.
Route Table
Route Table contains a set of rules, called route which helps us to route the network traffic.
A single VPC can have as many as route tables it requires.
If the dependencies are attached to the route table then they can’t be delete
Classless Inter-Domain Routing (CIDR)
A technique for allocating IP addresses and for IP routing is called classless Inter-Domain Routing (CIDR), and its range is 0-32.
When setting up a VPC, we must specify a set of IPv4 addresses using classless Inter-Domain Routing (CIDR), for (**Example:**10.0.0.0/16 For our VPC, this will serve as the main CIDR block).
NACL Network Access Control Lists
The NACL security layer for VPC serves as a firewall to manage traffic entering and leaving one or more subnets.
This is the Protection Layer of your subnet.
The NACL for the default VPC is active and connected to the default subnets.
e.g.Lets take some place where everyone can enter except some cases so same is the case with NACL.
NACL will allow everyone in your Network i.e.means it is Subnet Level protection.
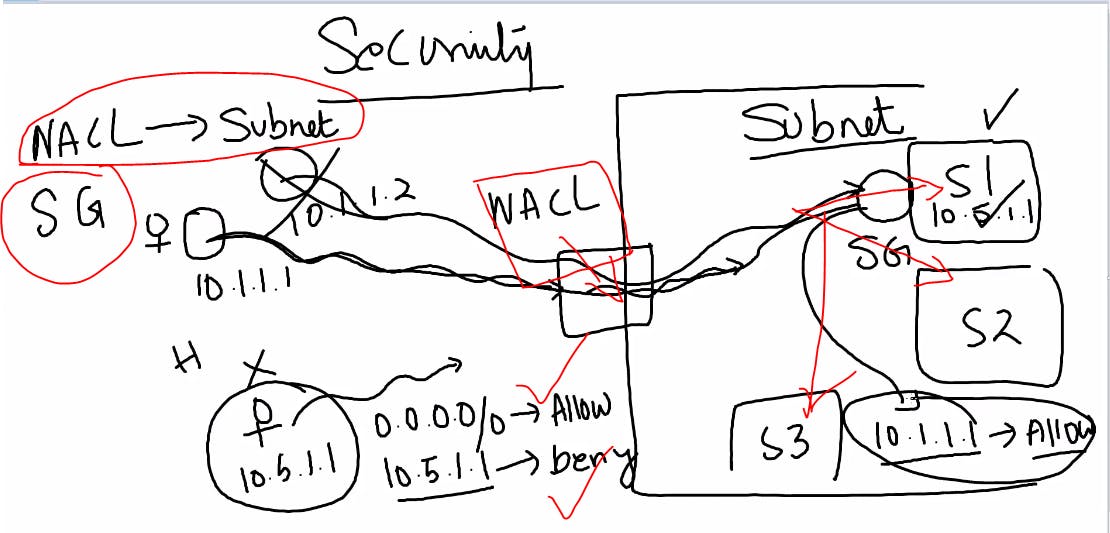
Security Group:(Whom to allow/deny can be set through SG)
Server Level Protection.
Only listed IP's/rules can be entered in Security group.
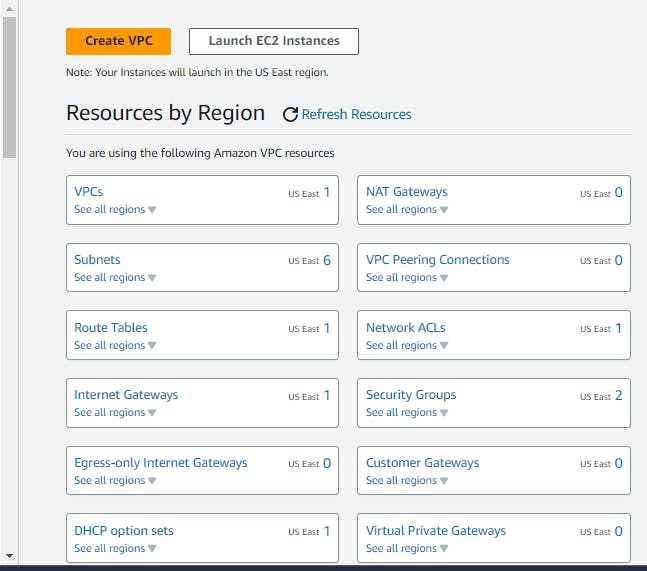
VPC Dashboard:
ELASTIC is a static
Public is a dynamic
If someone asks us to setup some Network
IP Creation depends on Requirement:
IPV4-10.2.1.4---4 Octates (4+4+4+4)bit
1 IP address is of 32 bit.
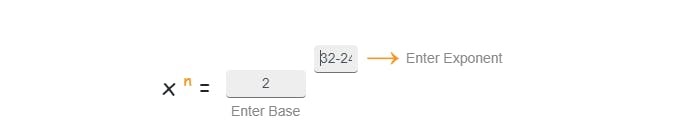
Lets calculate IP'S -10.0.0.0/24--we can say 24bits fixed
Formula:32-24=8 so (28)=256 IP's will gets created for this address.
10.0.0.0 -10.255.255.255 (10/8 prefix)
172.16.0.0 - 172.31.255.255 (172.16/12 prefix)
192.168.0.0 - 192.168.255.255 (192.168/16 prefix)
Private IP address Classes:
Class A:10.0.0.0--Very very large network
Class B:172.16---172.31--Large network
Class C:192.168--Small network
DHCP(Dynamic Host Configuration Protocol)
DHCP (Dynamic Host Configuration Protocol) is a network management protocol used to dynamically assign an IP address to any device, or node, on a network so it can communicate using IP. DHCP automates and centrally manages these configurations rather than requiring network administrators to manually assign IP addresses to all network devices. DHCP can be implemented on small local networks, as well as large enterprise networks.
e.g.If we are setting up an Network or Infra we cant manually check all the IP's in large network which is available and which is in use,to overcome this DHCP plays an important role It will allocate the IP's
NTP:(Network Time Protocol)
Its goal is to ensure that all computers on a network agree on the system clock since even a small difference can create problems. For example, if there is more than 5 minutes difference between your host’s local clock and the Active Directory domain controller, you cannot log into your AD domain.
e.g.Private network setup for organization
Network Time Protocol (NTP) is a protocol that helps the computers clock times to be synchronized in a network. This protocol is an application protocol that is responsible for the synchronization of hosts on a TCP/IP network. NTP was developed by David Mills in 1981 at the University of Delaware. This is required in a communication mechanism so that a seamless connection is present between the computers.
e.g.Any company like if something they change time on main server it should synchronize on all the internal servers with the help of NTP.
Features of NTP :
Some features of NTP are –
NTP servers have access to highly precise atomic clocks and GPU clocks
It uses Coordinated Universal Time (UTC) to synchronize CPU clock time.
Avoids even having a fraction of vulnerabilities in information exchange communication.
Provides consistent timekeeping for file server
E.g.Any network like lets take TCS,If something i
DNS(Domain Name Space)
In the world of networking, computers do not represent by names like humans do, they represent by numbers because that is how computers and other similar devices talk and identify with each other over a network, which is by using numbers such as IP addresses.
Humans on the other hand are accustomed to using names instead of numbers, whether is talking directly to another person or identifying a country, place, or things, humans identify with names instead of numbers. So in order to bridge the communication gap between computers and humans and make the communication of a lot easier networking engineers developed DNS.
A domain name serves as a distinctive identification for a website. To make it simpler for consumers to visit websites, it is used in place of an IP address.
A device connected to the internet is given an IP address, which is a numerical identity. It’s used to pinpoint where on the internet a website or gadget is.
An application called a DNS resolver is in charge of translating domain names into IP addresses. The DNS resolver contacts a DNS server to seek the IP address associated with a domain name when a user types it into their web browser.
DNS Server: A DNS server is a piece of software that keeps track of domain names and IP addresses. It answers with the appropriate IP address to requests from DNS resolvers.
The initial point of contact in the DNS system is a DNS root server. It offers details on the DNS servers in charge of top-level domains (TLDs), including.com,.org, and.net.
DNS resolves names to numbers, to be more specific it resolves domain names to IP addresses. So if you type in a web address in your web browser, DNS will resolve the name to a number because the only thing computers know are numbers.
OSI Model in a Nutshell
| Layer No | Layer Name | Responsibility | Information Form(Data Unit) | Device |
| 7 | Application Layer | Helps in identifying the client and synchronizing communication. | Message | – |
| 6 | Presentation Layer | Data from the application layer is extracted and manipulated in the required format for transmission. | Message | – |
| 5 | Session Layer | Establishes Connection, Maintenance, EnsuresAuthentication, and Ensures security. | Message | Gateway |
| 4 | Transport Layer | Take Service from Network Layer and provide it to the Application Layer. | Segment | Firewall |
| 3 | Network Layer | Transmission of data from one host to another, located in different networks. | Packet | Router |
| 2 | Data Link Layer | Node to Node Delivery of Message. | Frame | Switch, Bridge |
| 1 | Physical Layer | Establishing Physical Connections between Devices. | Bits | Hub, Repeater, Modem, Cables |
Layer 4- Transport Layer
The transport layer provides services to the application layer and takes services from the network layer. The data in the transport layer is referred to as Segments. It is responsible for the End to End Delivery of the complete message. The transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found.
At the sender’s side: The transport layer receives the formatted data from the upper layers, performs Segmentation, and also implements Flow & Error control to ensure proper data transmission. It also adds Source and Destination port numbers in its header and forwards the segmented data to the Network Layer.
Note: The sender needs to know the port number associated with the receiver’s application.
Generally, this destination port number is configured, either by default or manually. For example, when a web application requests a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default ports assigned.
Layer 7- Application Layer
At the very top of the OSI Reference Model stack of layers, we find the Application layer which is implemented by the network applications. These applications produce the data, which has to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user.
Example: Application – Browsers, Skype Messenger, etc.
Note: The application Layer is also called Desktop Layer.
Egress-only Internet gateway.(IPV6)
Use Cases
If you want your instance to be able to access the Internet, but you want to prevent resources on the Internet from initiating communication with your instance, you can use an egress-only Internet gateway.
To do this, create an egress-only Internet gateway in your VPC, and then add a route to your route table that points all IPv6 traffic (::/0) or a specific range of IPv6 address to the egress-only Internet gateway.
IPv6 traffic in the subnet that's associated with the route table is routed to the egress-only Internet gateway.
Stateless/Stateful Protocol:
Salient features of Stateless Protocols:
Stateless Protocol simplify the design of Server.
The stateless protocol requires less resources because system do not need to keep track of the multiple link communications and the session details.
In Stateless Protocol each information packet travel on it’s own without reference to any other packet.
Each communication in Stateless Protocol is discrete and unrelated to those that precedes or follow.
2. Stateful Protocol:
In Stateful Protocol If client send a request to the server then it expects some kind of response, if it does not get any response then it resend the request. FTP (File Transfer Protocol), TCP, and Telnet are the example of Stateful Protocol.
Salient features of Stateful Protocol:
Stateful Protocols provide better performance to the client by keeping track of the connection information.
Stateful Application require Backing storage.
Stateful request are always dependent on the server-side state.
TCP session follow stateful protocol because both systems maintain information about the session itself during its life.
Difference Between IPv4 and IPv6
| IPv4 | IPv6 |
| IPv4 has a 32-bit address length | IPv6 has a 128-bit address length |
| It Supports Manual and DHCP address configuration | It supports Auto and renumbering address configuration |
| In IPv4 end to end, connection integrity is Unachievable | In IPv6 end-to-end, connection integrity is Achievable |
| It can generate 4.29×109 address space | The address space of IPv6 is quite large it can produce 3.4×1038 address space |
| The Security feature is dependent on the application | IPSEC is an inbuilt security feature in the IPv6 protocol |
| Address representation of IPv4 is in decimal | Address Representation of IPv6 is in hexadecimal |
| Fragmentation performed by Sender and forwarding routers | In IPv6 fragmentation is performed only by the sender |
| In IPv4 Packet flow identification is not available | In IPv6 packet flow identification are Available and uses the flow label field in the header |
| In IPv4 checksum field is available | In IPv6 checksum field is not available |
| It has a broadcast Message Transmission Scheme | In IPv6 multicast and anycast message transmission scheme is available |
| In IPv4 Encryption and Authentication facility not provided | In IPv6 Encryption and Authentication are provided |
| IPv4 has a header of 20-60 bytes. | IPv6 has a header of 40 bytes fixed |
| IPv4 can be converted to IPv6 | Not all IPv6 can be converted to IPv4 |
| IPv4 consists of 4 fields which are separated by addresses dot (.) | IPv6 consists of 8 fields, which are separated by a colon (:) |
| IPv4’s IP addresses are divided into five different classes. Class A , Class B, Class C, Class Da , Class E. | IPv6 does not have any classes of the IP address. |
| IPv4 supports VLSM(Variable Length subnet mask). | IPv6 does not support VLSM. |
| Example of IPv4: 66.94.29.13 | Example of IPv6: 2001:0000:3238:DFE1:0063:0000:0000:FEFB |
Ports:
80--HTTP
443--SSH
22--HTTPS
VPC Hands on:
VPC is a Region Based
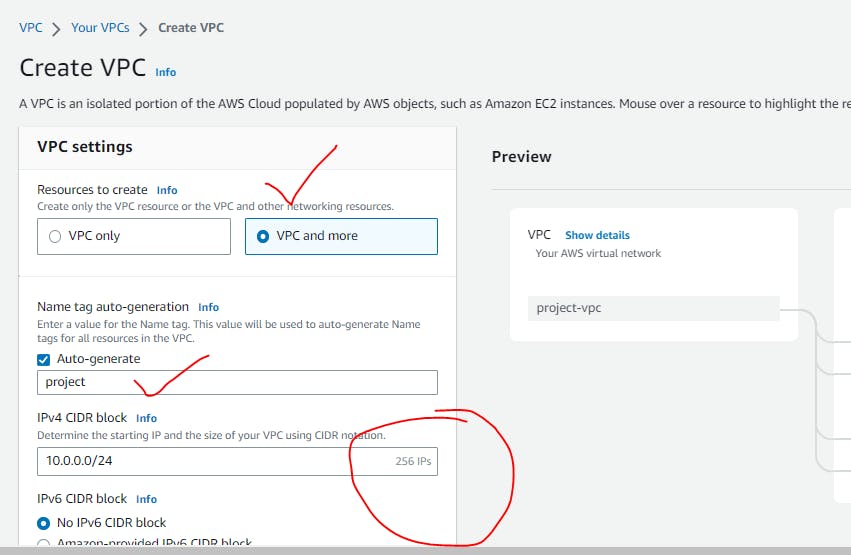
Select VPC and More as we are creating all the things.
Provide CIDR blocks as how many IP's you need
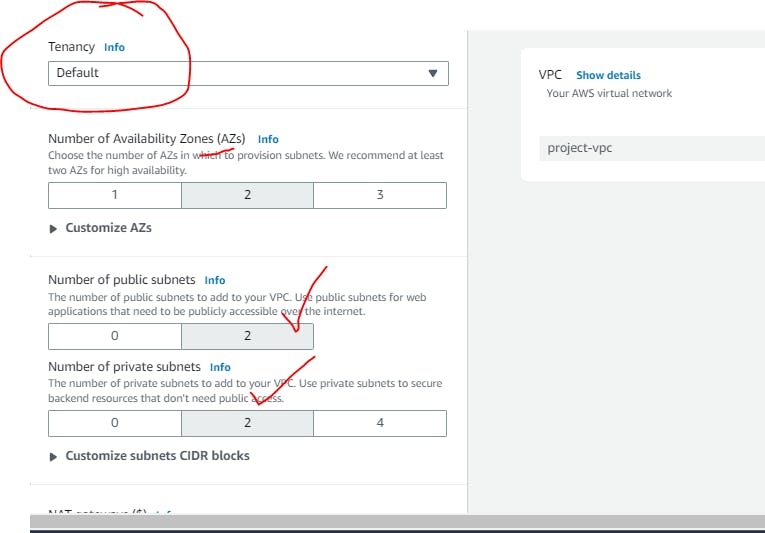
Tenancy means if you want dedicated server once it gets created.
Default recommended as Dedicated is chargable.
Select count for Private/Public Subnet
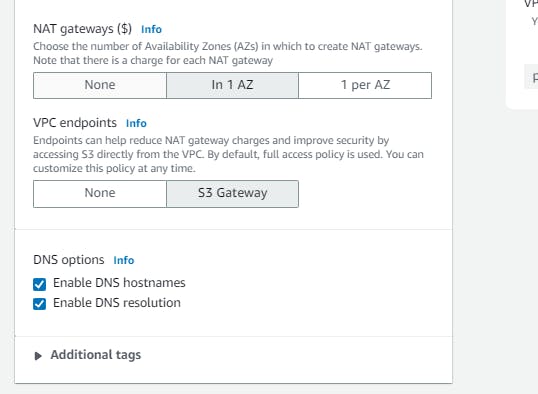
An S3 VPC endpoint provides a way for an S3 request to be routed through to the Amazon S3 service, without having to connect a subnet to an internet gateway. The S3 VPC endpoint is what's known as a gateway endpoint
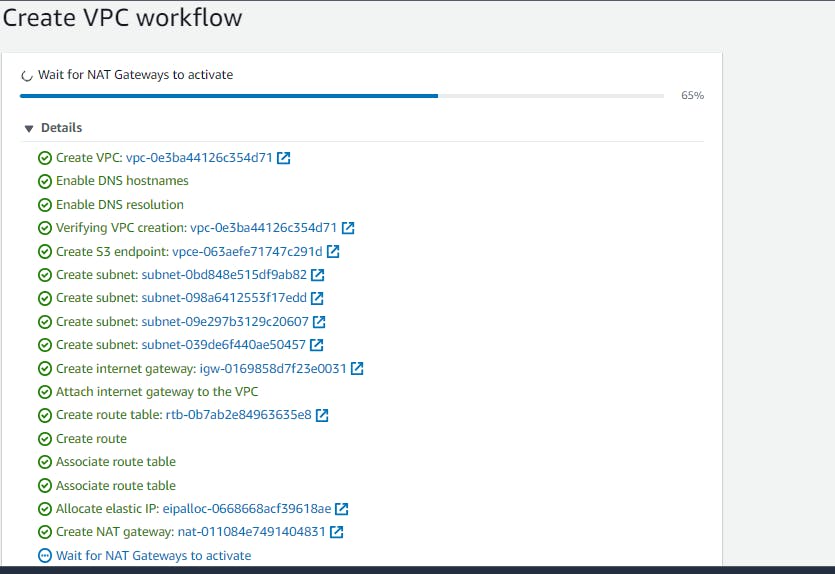
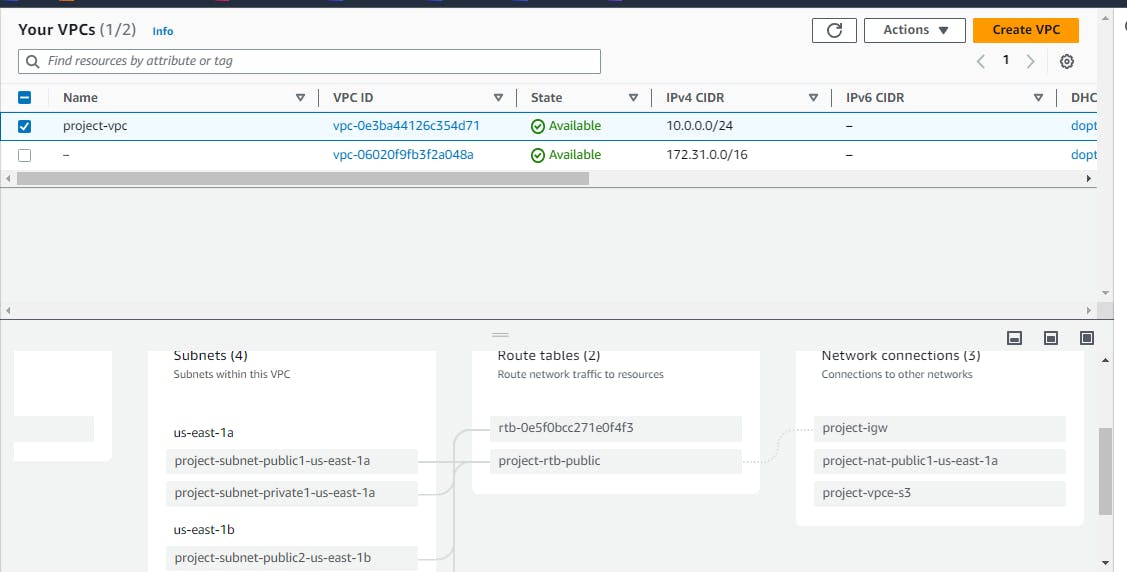
Here is your own Network!
VPC Peering
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account. It is logically isolated from other virtual networks in the AWS Cloud. You can launch AWS resources, such as Amazon EC2 instances, into your VPC.
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them using private IPv4 addresses or IPv6 addresses. Instances in either VPC can communicate with each other as if they are within the same network. You can create a VPC peering connection between your own VPCs, or with a VPC in another AWS account. The VPCs can be in different Regions (also known as an inter-Region VPC peering connection).
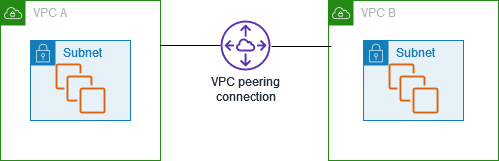
AWS uses the existing infrastructure of a VPC to create a VPC peering connection; it is neither a gateway nor a VPN connection, and does not rely on a separate piece of physical hardware. There is no single point of failure for communication or a bandwidth bottleneck.
A VPC peering connection helps you to facilitate the transfer of data. For example, if you have more than one AWS account, you can peer the VPCs across those accounts to create a file sharing network. You can also use a VPC peering connection to allow other VPCs to access resources you have in one of your VPCs.
When you establish peering relationships between VPCs across different AWS Regions, resources in the VPCs (for example, EC2 instances and Lambda functions) in different AWS Regions can communicate with each other using private IP addresses, without using a gateway, VPN connection, or network appliance. The traffic remains in the private IP space. All inter-Region traffic is encrypted with no single point of failure, or bandwidth bottleneck. Traffic always stays on the global AWS backbone, and never traverses the public internet, which reduces threats, such as common exploits, and DDoS attacks. Inter-Region VPC peering provides a simple and cost-effective way to share resources between regions or replicate data for geographic redundancy.
Linkdin:https://www.linkedin.com/in/gajanan-barure-7351a4140✔️
***Happy Learning :)***✌✌
Keep learning,Keep growing🎇🎇
Thank you for reading!! Hope you find this helpful.
#awscloud#90daysofdevops#devopscommunity#awscommunity
