Table of contents
- KMS(Key Management Service):
- Features of AWS KMS
- Types of Keys:
- What is DNS root server?
- Why are there only 13 DNS root server addresses?
- What happens if a DNS root server becomes unavailable?
- Hands on KMS:
- Here you go!
- Rotating AWS KMS keys:
- What is SSL?
- What is AWS Secrets Manager?
- What is Amazon SDK used?
- Successfully Stored Secrets:
- How it is different from Cloud KMS:
- AWS KMS vs Azure Key Vault vs Google Cloud KMS:
KMS(Key Management Service):
AWS provides multiple services among which KMS provides security or sensitive data encryption on Server side.
Key Management Service is used to encrypt data in AWS. The main purpose of the AWS KMS is to store and manage those encryption keys. Data encryption is vital if you have sensitive data that must not be accessed by unauthorized users. Implement data encryption for both data at rest and data in transit.
Features of AWS KMS
It is an easy way to control and access your data using managed encryption.
With AWS Key Management Service, the process of key management is reduced to a few simple clicks.
It is also integrated with other AWS services including Amazon EBS, Amazon S3, and Amazon RedShift to simplify the encryption of your data within these services.
AWS KMS enables you to create, rotate, disable, enable, and define usage policies for master keys and audit their usage.
It is a centralized key management
It is secure and compliant.
Two main methods to implement encryption at rest are Client-Side Encryption and Server Side Encryption.
Client-Side Encryption is where you can encrypt the data on the client side and send it all the way to the server or any backend services like S3, EBS, Redshift, etc. In short, we can say in client-side encryption you encrypt your data and manage your own keys.
Server-Side Encryption AWS encrypts the data and manages the keys for you, whereas you let your backend services encrypt the data and manage those keys on your behalf.
Types of Keys:
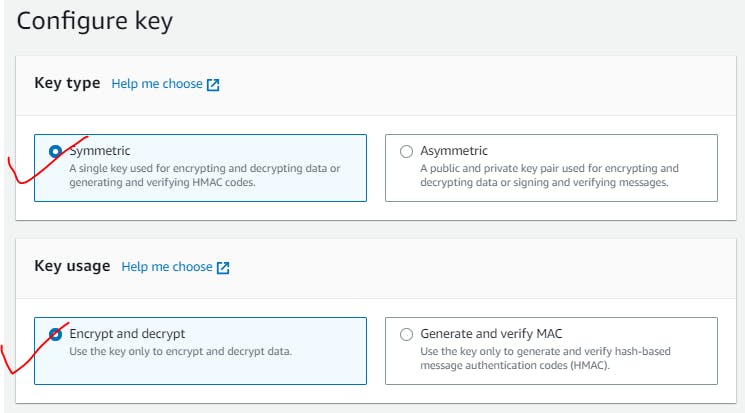
1.Symmetric Key
You need one Cetificate/Key for Encryption/Decryption.
2.Asymmetric Key
Separate keys for Encryption and Decryption
E.g.Lets suppose if we hit google.com 1st it will search for host file in system then next it will go for route server if private server it will go to NATthen It will go to IGW.
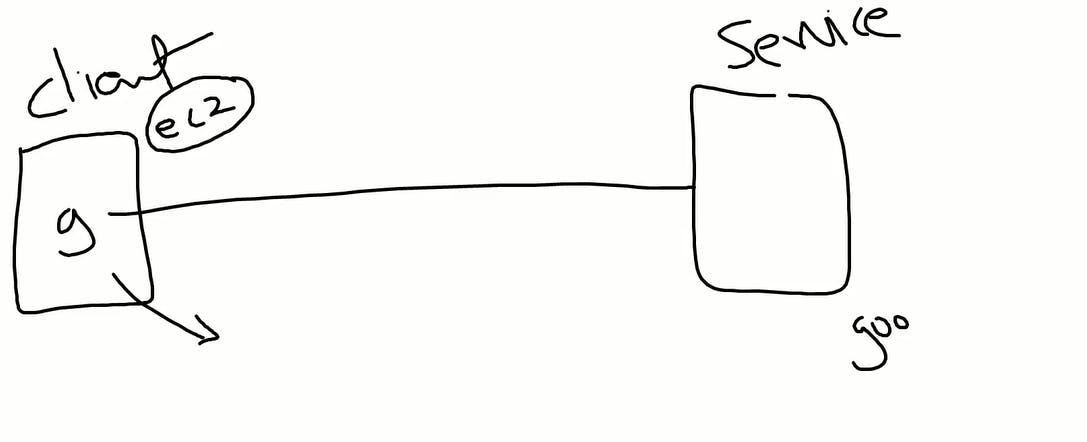
So here is the DNS root server( 13 root servers) topic comes in the picture.
What is DNS root server?
The administration of the Domain Name System (DNS) is structured in a hierarchy using different managed areas or “zones”, with the root zone at the very top of that hierarchy. Root servers are DNS nameservers that operate in the root zone. These servers can directly answer queries for records stored or cached within the root zone, and they can also refer other requests to the appropriate Top Level Domain (TLD) server. The TLD servers are the DNS server group one step below root servers in the DNS hierarchy, and they are an integral part of resolving DNS queries.
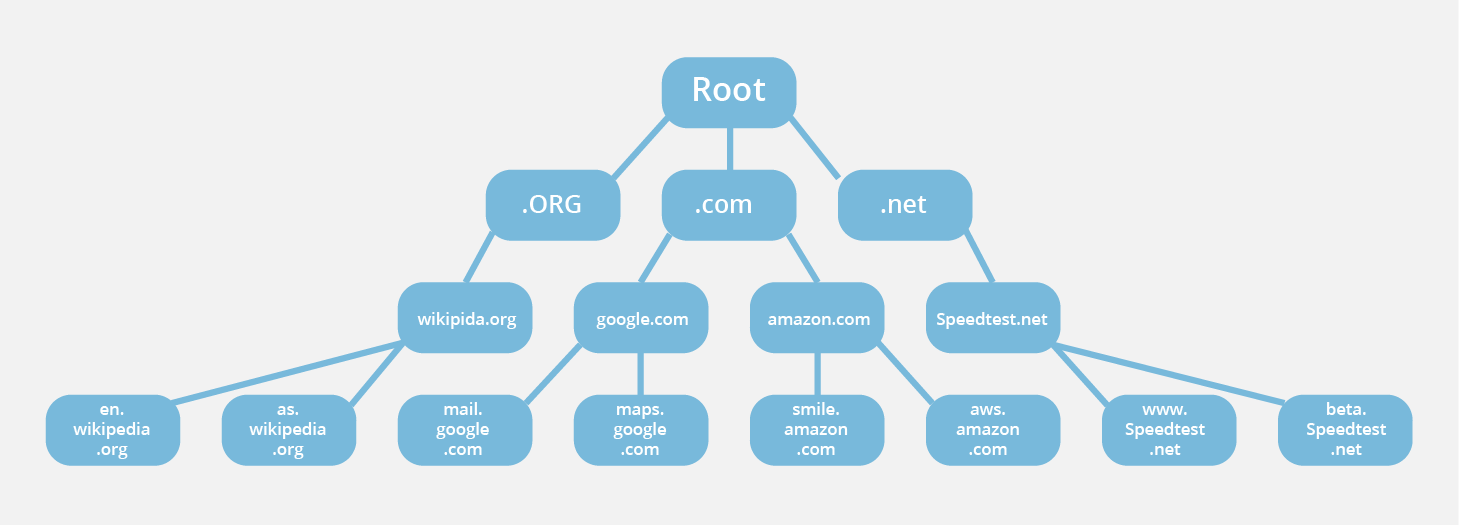
During an uncached DNS query, whenever a user enters a web address into their browser, this action triggers a DNS lookup, and all DNS lookups start at the root zone. Once the lookup hits the root zone, the lookup will then travel down the hierarchy of the DNS system, first hitting the TLDs servers, then the servers for specific domains (and possibly subdomains) until it finally hits the authoritative nameserver for the correct domain, which contains the numerical IP address of the website being sought. This IP address is then returned to the client. Interestingly, despite the number of steps required, this process can happen very quickly.
Root servers are an essential part of the infrastructure of the Internet; web browsers and many other internet tools would not work without them. There are 13 different IP addresses that serve the DNS root zone, and hundreds of redundant root servers exist around the globe to handle requests to the root zone.
Why are there only 13 DNS root server addresses?
A common misconception is that there are only 13 root servers in the world. In reality there are many more, but still only 13 IP addresses used to query the different root server networks. Limitations in the original architecture of DNS require there to be a maximum of 13 server addresses in the root zone. In the early days of the Internet, there was only one server for each of the 13 IP addresses, most of which were located in the United States.
Today each of the 13 IP addresses has several servers, which use Anycast routing to distribute requests based on load and proximity. Right now there are over 600 different DNS root servers distributed across every populated continent on earth.
What happens if a DNS root server becomes unavailable?
Thanks to the use of Anycast routing and heavy redundancy, the root servers are very reliable. But on rare occasions a root server will have to update its IP address. In this case, recursive resolvers can continue using the other 12 IP addresses in the root zone to perform DNS lookups until their software is updated with the correct addresses of all 13 servers. Since resolvers will retry until they reach a working root server, there is no disruption to the normal operations of the Internet when one root server is down. Learn more about how Cloudflare DNS uses Anycast routing to improve reliability.
Hands on KMS:
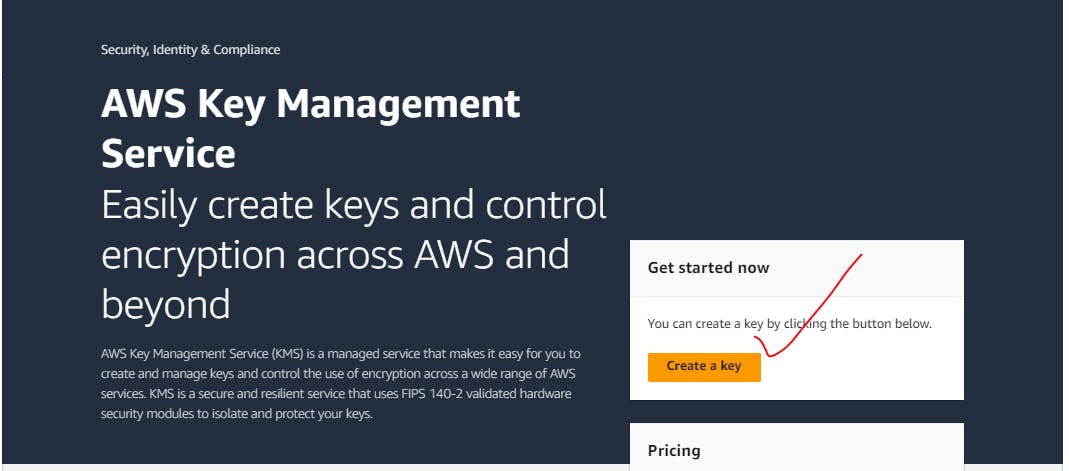
Symmetric Key same key for Encryption/Decryption:
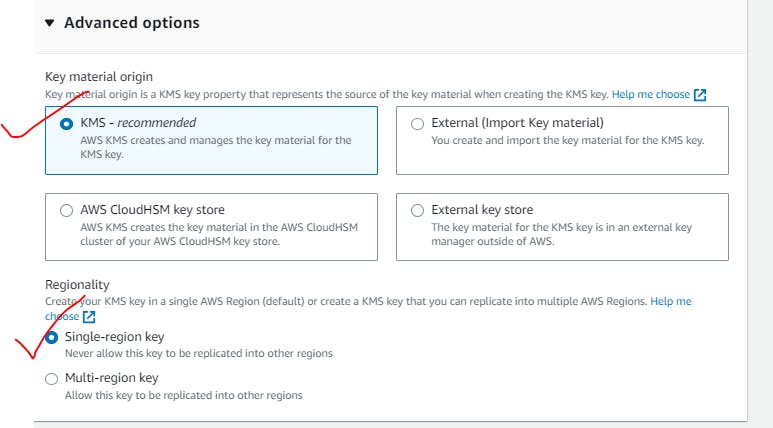
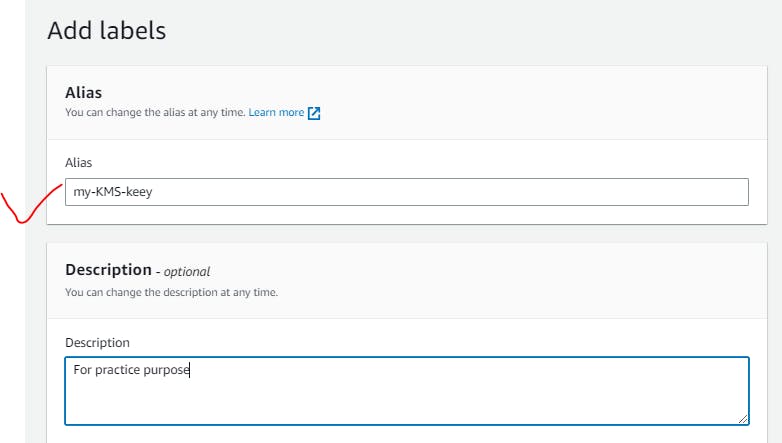
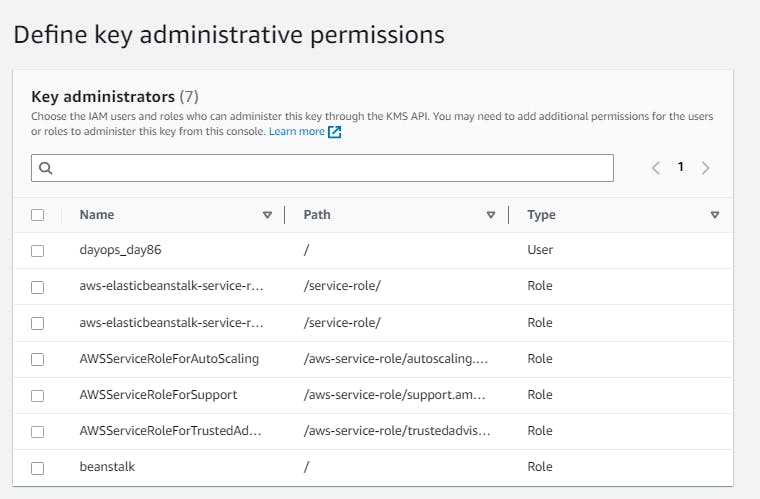
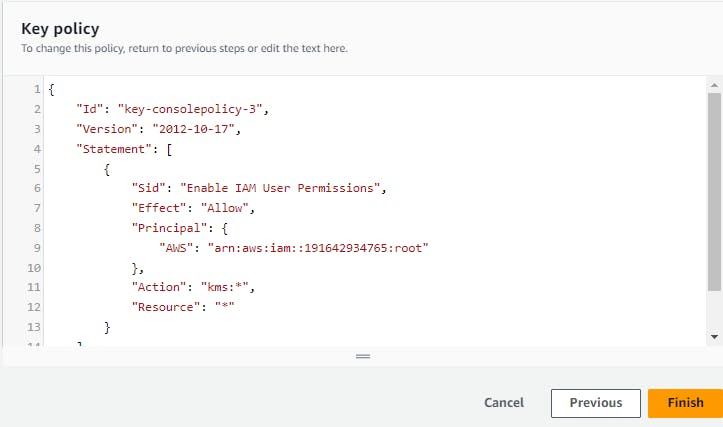
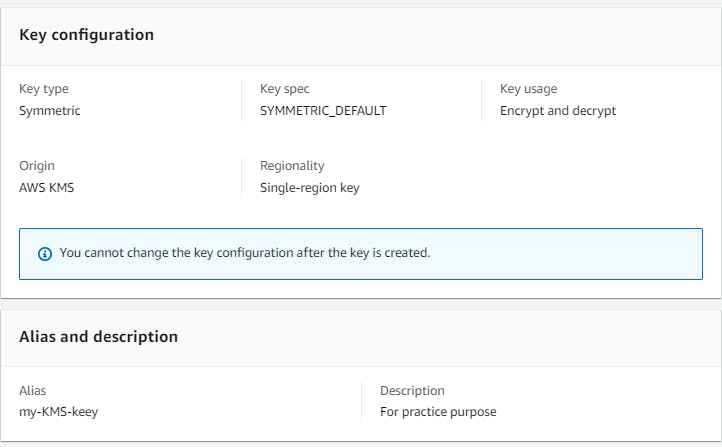
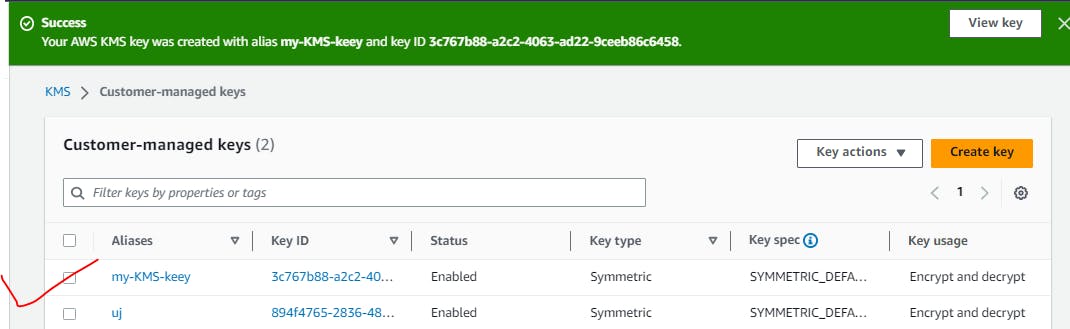
So this key can be used to encrypt your data like in S3,EC2.
e.g.Let's add additional encryption on S3 bucket.
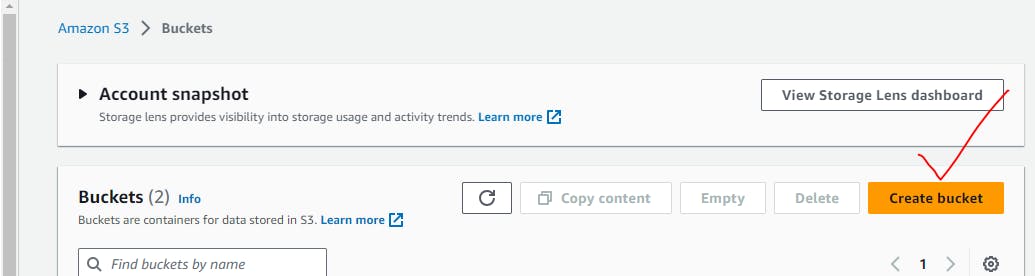
Here you go!
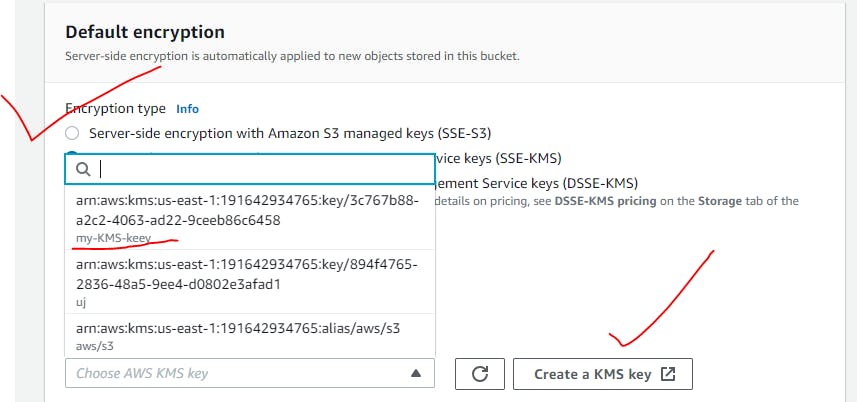
Rotating AWS KMS keys:
When you enable automatic key rotation for a KMS key, AWS KMS generates new cryptographic material for the KMS key every year. AWS KMS saves all previous versions of the cryptographic material in perpetuity so you can decrypt any data encrypted with that KMS key. AWS KMS does not delete any rotated key material until you delete the KMS key. You can track the rotation of key material for your KMS keys in Amazon CloudWatch and AWS CloudTrail.
E.g.It is like changing passwords in organization for every three months,AWS KMS will take care of that as lets suppose if our pin is in between 0000-9999 if 10k permutations combinations tried it is easy to hack ,so same concept here KMS will generate Certifications/key and rotate every year.
What is SSL?
SSL certificates are what enable websites to use HTTPS, which is more secure than HTTP. An SSL certificate is a data file hosted in a website's origin server. SSL certificates make SSL/TLS encryption possible, and they contain the website's public key and the website's identity, along with related information.
Devices attempting to communicate with the origin server will reference this file to obtain the public key and verify the server's identity. The private key is kept secret and secure.
What is SSL?
SSL, more commonly called TLS, is a protocol for encrypting Internet traffic and verifying server identity. Any website with an HTTPS web address uses SSL/TLS.
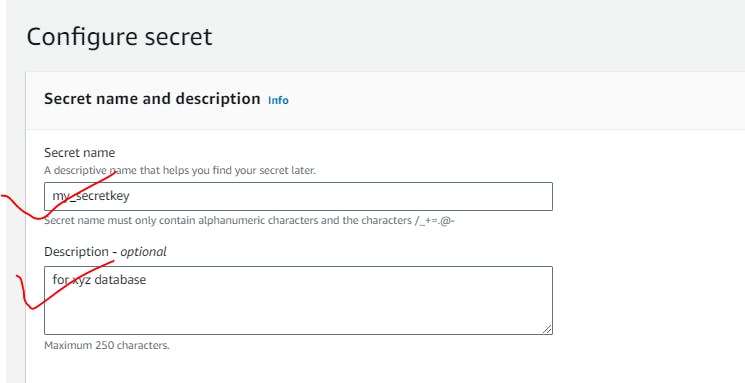
What is AWS Secrets Manager?
AWS Secrets Manager is a secrets management service that helps you protect access to your applications, services, and IT resources. This service enables you to easily rotate, manage, and retrieve database credentials, API keys, and other secrets throughout their lifecycle. Using Secrets Manager, you can secure and manage secrets used to access resources in the AWS Cloud, on third-party services, and on-premises.
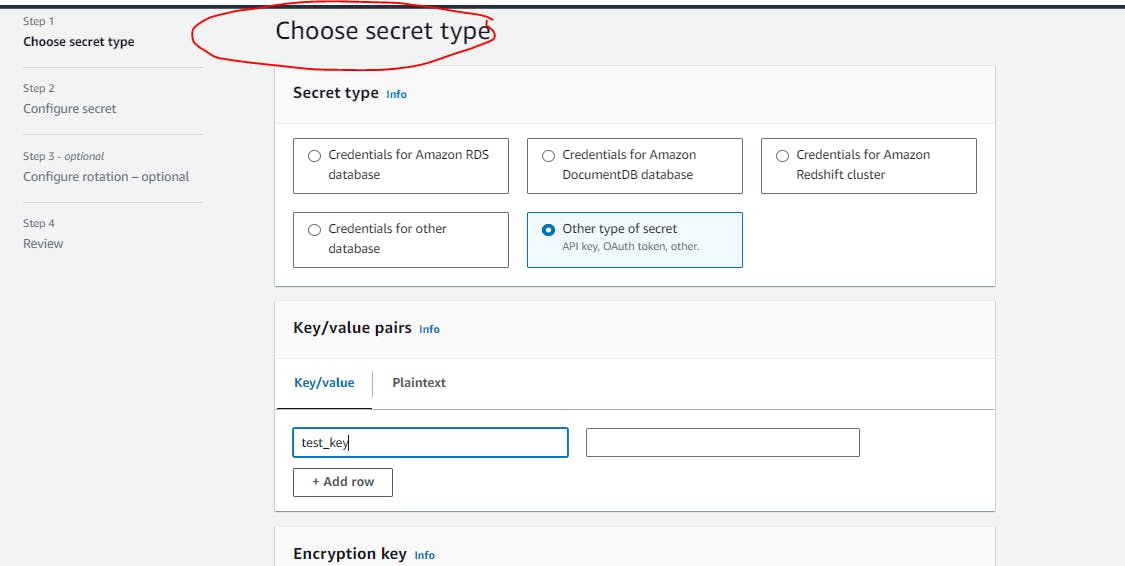
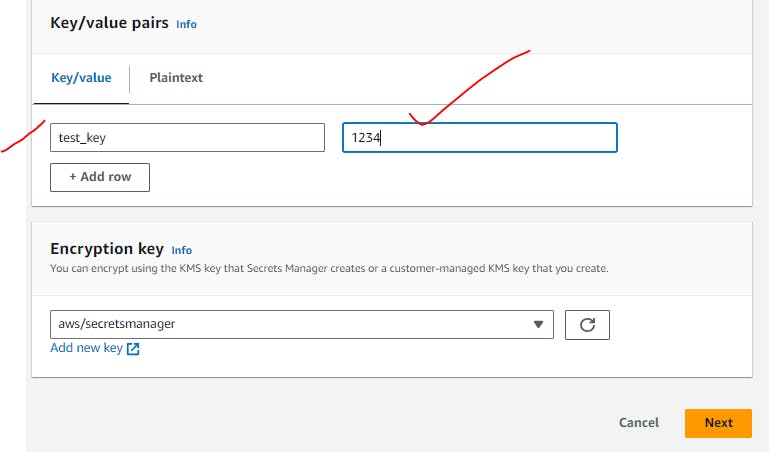
Secrets can be used in our code by below codes:
What is Amazon SDK used?
The AWS SDK (software development kit) simplifies the whole programming experience by providing JavaScript objects for AWS services. It enables developers to use AWS via JavaScript code that runs in the browser, and it offers access to AWS components such as Amazon S3, Amazon SNS, Amazon SQS, DynamoDB, and others.

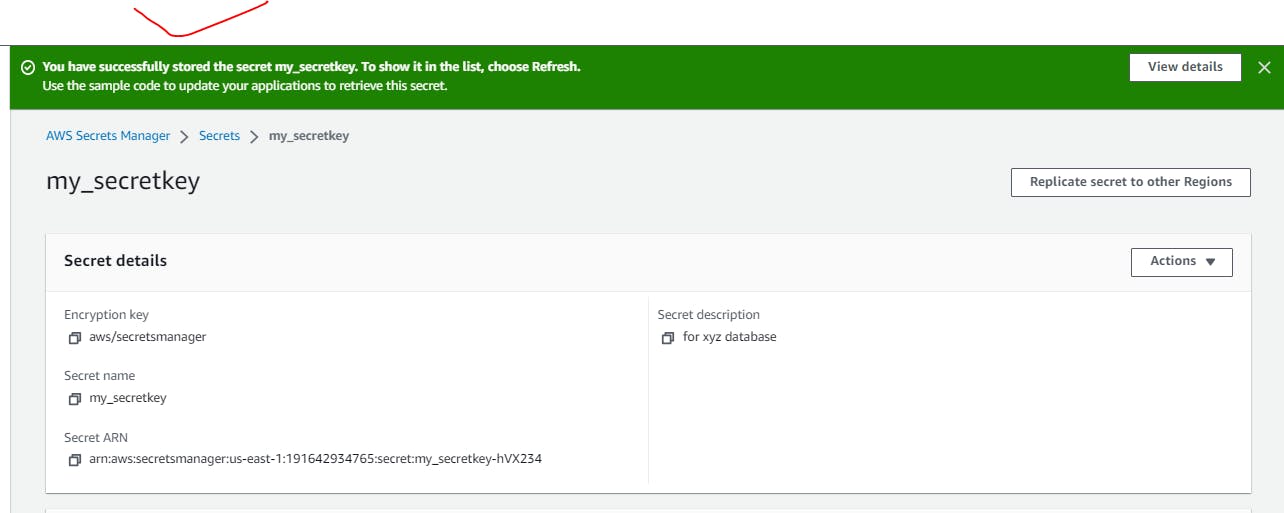
Successfully Stored Secrets:
Same can be Created with AWS CLI also:
Steps:
Install AWS CLI and run below command and verify in console if gets stored or not.
Command:apt-get install awscli
For creating the secret run the following command: $ aws secretsmanager create-secret --name tutorial/firstkey 2 --description "Basic Create Secret" --secret-string '{"testkey":"testvalue"}'
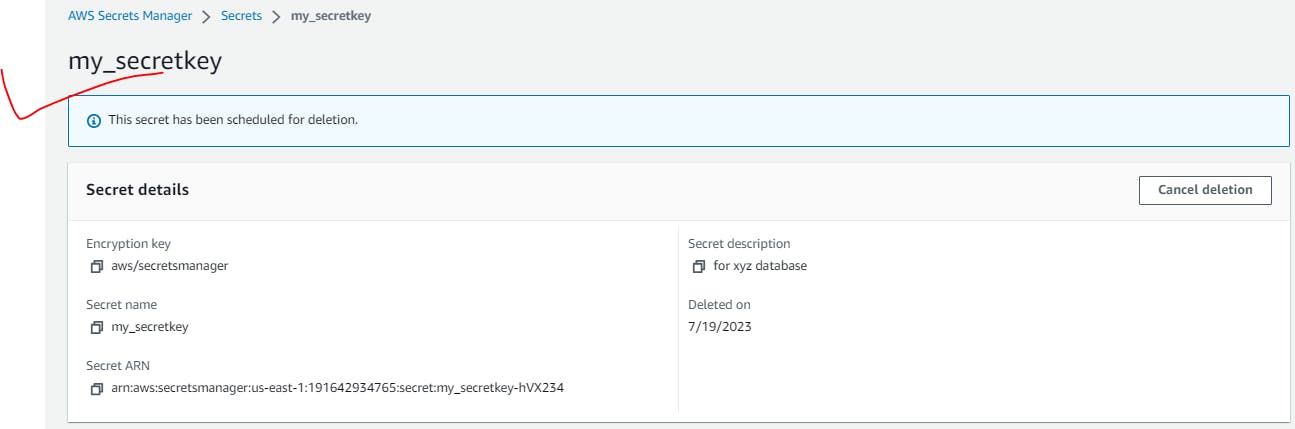
Delete once you are done with task:
How it is different from Cloud KMS:
Cloud KMS(Key Management Service) is a service that is used to create and manage cryptographic keys. It follows the encryption and decryption process whereas the Secret Manager stores the credentials in a vault (secret) instead of encrypting and decrypting them.
You can use KMS keys to encrypt things such as files, strings, and s3 objects.
SecretsManager stores actual secrets like passwords and such.
AWS KMS vs Azure Key Vault vs Google Cloud KMS:
| # | Feature | AWS KMS | Azure Key Vault | Google Cloud KMS |
| 1 | Key Storage | Appliance (Software + Hardware) | Appliance* (Software) | Appliance (Software + Hardware) |
| 2 | FIPS 140-2 Level | Level 2 | Level 2 | Level 1 |
| 3 | Key Types | Symmetric and Asymmetric | Asymmetric | Symmetric and Asymmetric |
| 4 | BYOK (Bring Your Own Key) | AES 256-bit wrapped by RSA 2048-bit | RSA wrapped by AES and RSA-OAEP | AES 256-bit wrapped by RSA 3072-bit |
| 5 | Symmetric Key Length | 256-bit AES | None | 256-bit AES |
| 6 | Asymmetric Key Length | 2048-bit, 3072-bit, 4096-bit RSA | 2048-bit, 3072-bit, 4096-bit RSA | 2048-bit, 3072-bit, 4096-bit RSA |
| 7 | Encryption Modes | AES-GCM, RSA-OAEP | AES-GCM, RSA-OAEP | RSA PKCS#1v1.5, RSA-OAEP |
| 8 | Plain-text size limit | 4KB | 0.25KB | 64KB |
| 9 | Signature Modes | RSA-PSSRSA PKCS#1v1.5ECDSA with P-256ECDSA with P-384ECDSA with P-512ECDSA with SECP-256k1 | RSA-PSSRSA PKCS#1v1.5ECDSA with P-256ECDSA with P-384ECDSA with P-512ECDSA with SECP-256k1 | RSA-PSSRSA PKCS#1v1.5ECDSA with P-256ECDSA with P-384 |
| 10 | Key Capabilities | AWS Managed ServiceEncryption/DecryptionSign/VerifyAuditingREST APIs | Support Customer Managed KeysSupport tokens, passwords, certificates, API keys, and other secretsEncryption/DecryptionSign/VerifyKey Vault loggingREST APIs | Support Customer Managed KeysEncryption/DecryptionSign/VerifyAuditingREST APIs |
Linkdin:https://www.linkedin.com/in/gajanan-barure-7351a4140✔️
***Happy Learning :)***✌✌
Keep learning,Keep growing🎇🎇
Thank you for reading!! Hope you find this helpful.
#awscloud#90daysofdevops#devopscommunity#awscommunity#Secrets
