By this time you have created multiple EC2 instances, and post installation manually installed applications like Jenkins, docker etc. Now let's switch to little automation part. Sounds interesting??🤯
AWS:
Amazon Web Services (AWS) is the world’s most comprehensive and broadly adopted cloud, offering over 200 fully featured services from data centers globally. Millions of customers—including the fastest-growing startups, largest enterprises, and leading government agencies—are using AWS to lower costs, become more agile, and innovate faster.
Most functionality:
AWS also has the deepest functionality within those services. For example, AWS offers the widest variety of databases that are purpose-built for different types of applications so you can choose the right tool for the job to get the best cost and performance.
Most secure
AWS is architected to be the most flexible and secure cloud computing environment available today. Our core infrastructure is built to satisfy the security requirements for the military, global banks, and other high-sensitivity organizations. This is backed by a deep set of cloud security tools, with over 300 security, compliance, and governance services and features. AWS supports 98 security standards and compliance certifications, and all 117 AWS services that store customer data offer the ability to encrypt that data.
Global network of AWS Regions
AWS has the most extensive global cloud infrastructure. The AWS Region and Availability Zone model has been recognized
by Gartner as the recommended approach for running enterprise applications that require high availability.

| Code | Name | Opt-in Status |
us-east-2 | US East (Ohio) | Not required |
us-east-1 | US East (N. Virginia) | Not required |
us-west-1 | US West (N. California) | Not required |
us-west-2 | US West (Oregon) | Not required |
af-south-1 | Africa (Cape Town) | Required |
ap-east-1 | Asia Pacific (Hong Kong) | Required |
ap-south-2 | Asia Pacific (Hyderabad) | Required |
ap-southeast-3 | Asia Pacific (Jakarta) | Required |
ap-southeast-4 | Asia Pacific (Melbourne) | Required |
ap-south-1 | Asia Pacific (Mumbai) | Not required |
ap-northeast-3 | Asia Pacific (Osaka) | Not required |
ap-northeast-2 | Asia Pacific (Seoul) | Not required |
ap-southeast-1 | Asia Pacific (Singapore) | Not required |
ap-southeast-2 | Asia Pacific (Sydney) | Not required |
ap-northeast-1 | Asia Pacific (Tokyo) | Not required |
ca-central-1 | Canada (Central) | Not required |
eu-central-1 | Europe (Frankfurt) | Not required |
eu-west-1 | Europe (Ireland) | Not required |
eu-west-2 | Europe (London) | Not required |
eu-south-1 | Europe (Milan) | Required |
eu-west-3 | Europe (Paris) | Not required |
eu-south-2 | Europe (Spain) | Required |
eu-north-1 | Europe (Stockholm) | Not required |
eu-central-2 | Europe (Zurich) | Required |
me-south-1 | Middle East (Bahrain) | Required |
me-central-1 | Middle East (UAE) | Required |
sa-east-1 | South America (São Paulo) | Not required |
Availability Zone
Each Region has multiple, isolated locations known as Availability Zones. The code for Availability Zone is its Region code followed by a letter identifier. For example, us-east-1a.
When you launch an instance, you select a Region and a virtual private cloud (VPC), and then you can either select a subnet from one of the Availability Zones or let us choose one for you. If you distribute your instances across multiple Availability Zones and one instance fails, you can design your application so that an instance in another Availability Zone can handle requests. You can also use Elastic IP addresses to mask the failure of an instance in one Availability Zone by rapidly remapping the address to an instance in another Availability Zone.
The following diagram illustrates multiple Availability Zones in an AWS Region. Availability Zone A and Availability Zone B each have one subnet, and each subnet has instances. Availability Zone C has no subnets, therefore you can't launch instances into this Availability Zone.
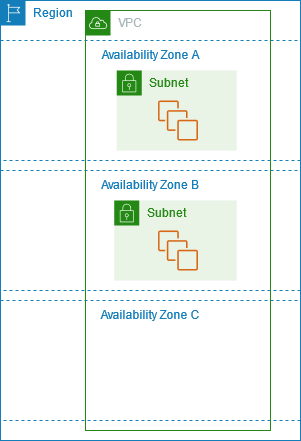
As Availability Zones grow over time, our ability to expand them can become constrained. If this happens, we might restrict you from launching an instance in a constrained Availability Zone unless you already have an instance in that Availability Zone. Eventually, we might also remove the constrained Availability Zone from the list of Availability Zones for new accounts. Therefore, your account might have a different number of available Availability Zones in a Region than another account.
User Data in AWS:
When you launch an instance in Amazon EC2, you have the option of passing user data to the instance that can be used to perform common automated configuration tasks and even run scripts after the instance starts. You can pass two types of user data to Amazon EC2: shell scripts and cloud-init directives.
You can also pass this data into the launch instance wizard as plain text, as a file (this is useful for launching instances using the command line tools), or as base64-encoded text (for API calls).
This will save time and manual effort everytime you launch an instance and want to install any application on it like apache, docker, Jenkins etc.
IAM:
AWS Identity and Access Management (IAM) is a web service that helps you securely control access to AWS resources. With IAM, you can centrally manage permissions that control which AWS resources users can access. You use IAM to control who is authenticated (signed in) and authorized (has permissions) to use resources.
IAM stands for Identity Access Management.
IAM allows you to manage users and their level of access to the aws console.
It is used to set users, permissions and roles. It allows you to grant access to the different parts of the aws platform.
AWS Identity and Access Management is a web service that enables Amazon Web Services (AWS) customers to manage users and user permissions in AWS.
With IAM, Organizations can centrally manage users, security credentials such as access keys, and permissions that control which AWS resources users can access.
Without IAM, Organizations with multiple users must either create multiple user accounts, each with its own billing and subscriptions to AWS products or share an account with a single security credential. Without IAM, you also don't have control about the tasks that the users can do.
IAM enables the organization to create multiple users, each with its own security credentials, controlled and billed to a single aws account. IAM allows the user to do only what they need to do as a part of the user's job.
What are the 3 types of IAM principals?
Principals: Three types of Principals — root users, IAM users and Instance Principals.

Authentication in IAM
Authentication or identity management in AWS IAM consists of the following identities:
Users: An IAM user interacts with your AWS resources from the AWS console and the AWS CLI. By default, a new IAM user has no access to any AWS resource.
Groups: An IAM group consists of IAM users and permissions assigned to those users.
Roles: An IAM role is an entity with a specific set of permissions.
Authorization in IAM
IAM Policies determine authorization or access management in IAM by granting specific permissions to various IAM identities.
What is an IAM Role?
An IAM role is an IAM identity that you can create in your AWS account and assign specific permissions.
An IAM role is similar to an IAM because it is an IAM identity that has specific permissions associated with it. These permissions determine what the identity can and cannot do.
However, one significant difference between an IAM role and an IAM user is that a role is assumable by anyone who needs it. A role does not have standard long-term credentials (like passwords) associated with it. AWS generates temporary security credentials when an IAM role is assumed.
What is an IAM Policy?
An IAM policy is a document with a set of rules. Each IAM policy grants a specific set of permissions.
Policies are attached to IAM identities like Users, Groups, and Roles. Each IAM policy has a unique name.
There are two types of policies in your AWS account:
Managed policies: These policies can be reused and attached to multiple entities. AWS provides a lot of managed policies by default. Customers can also create their own managed policies.
Inline policies: These policies are applied directly to IAM entities. However, these policies are not reusable and cannot be attached to multiple entities.
IAM Roles vs. Policies
IAM Roles manage who has access to your AWS resources, whereas IAM policies control their permissions.
A Role with no Policy attached to it won’t have to access any AWS resources.
A Policy that is not attached to an IAM role is effectively unused. Permissions listed in an IAM policy are only enforced when that policy is attached to an IAM identity.
Therefore, you should IAM roles and policies together to manage the security of your AWS resources.
Task1:
Launch EC2 instance with already installed Jenkins on it. Once server shows up in console, hit the IP address in browser and you Jenkins page should be visible.
Take screenshot of Userdata and Jenkins page, this will verify the task completion.




Task2:
Read more on IAM Roles and explain the IAM Users, Groups and Roles in your own terms.
Create three Roles named: DevOps-User, Test-User and Admin.



DevOps user:


Test User:

Admin:

All the roles as below:

Now you can create a users/EC2 and assign the roles to them.
Conclusion:Launched instance with already installed jenkins on it i.e.written script for jenkins installation under user data,then created three roles so that it will be easier to sort out the roles and provide specific access according to the roles.
Thank you for reading!! Hope you find this helpful.
#day39#90daysofdevops#devopscommunity#
Always open for suggestions..!!
